Running Pentests
Learn how pentests work, how to start them, and monitor progress
How Pentests Work
ModernPentest uses intelligent agents that automatically adapt to your application's configuration:
Surface-Based Testing
Agents are assigned based on your configured attack surfaces:
Web Applications
- A reconnaissance agent maps your site, discovering pages, forms, and technologies
- Security testing agents are dynamically spawned based on discovered content
- Testing adapts to what's found during reconnaissance
REST APIs
- Endpoints are intelligently grouped by feature domain
- Specialized agents test for BOLA, authentication flaws, and injection vulnerabilities
- Each agent group runs in parallel for faster results
Pentest duration varies based on application size. A small API might complete in 10-15 minutes, while a large web application could take 30-60 minutes.
Starting a Pentest
- Go to the Applications page
- Find your application card
- Click Start Pentest
- You'll be redirected to the pentest monitoring page
Each application can only have one pentest running at a time. Complete or wait for the current pentest before starting another.
Monitoring Progress
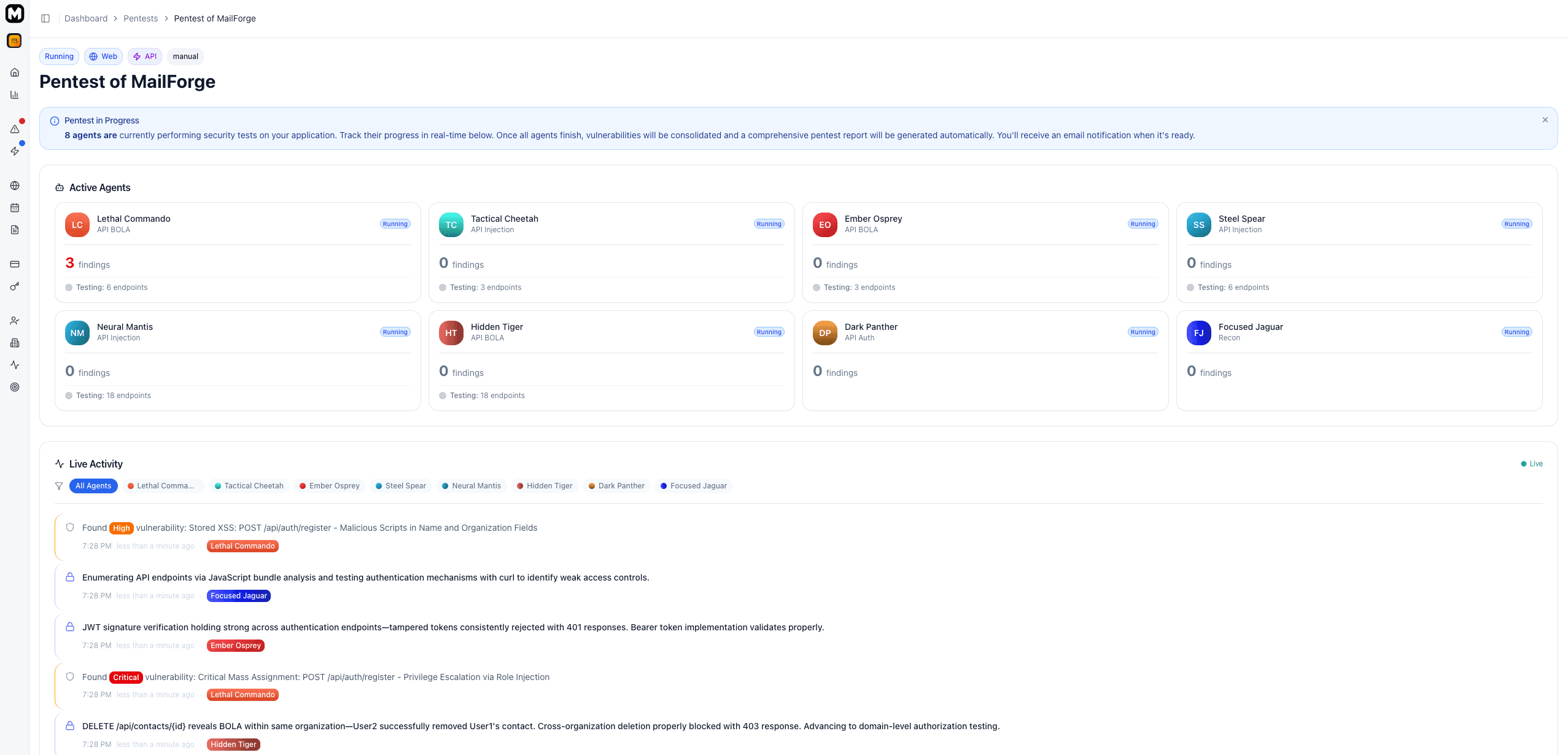
Once started, monitor your pentest in real-time on the pentest detail page:
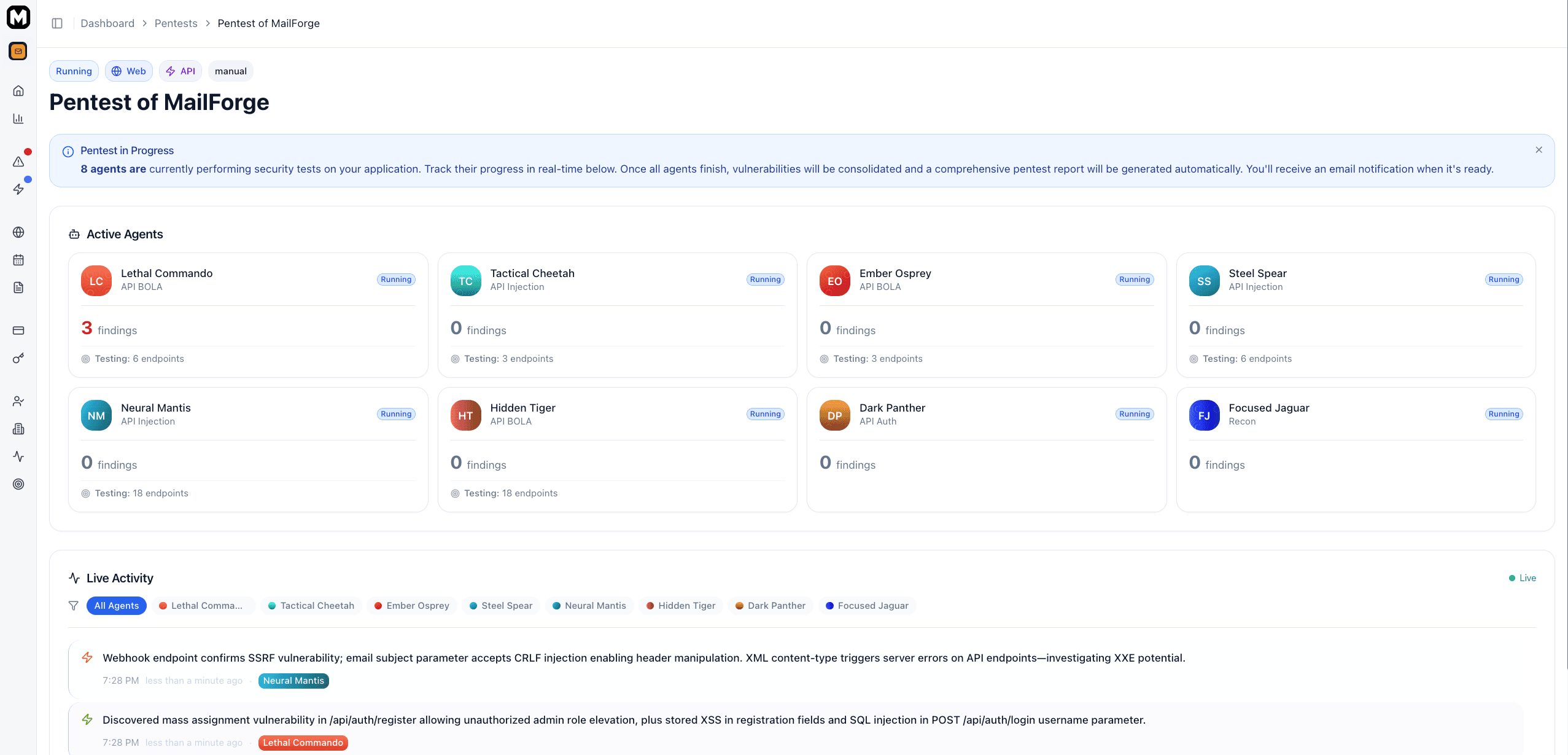
Live Dashboard
The pentest dashboard shows:
- Current status - Pending, Running, Processing, or Completed
- Active agents - Which security agents are currently testing
- Agent activity - Real-time logs of what's being tested
- Live findings - Vulnerabilities as they're detected
Agent Pipeline
Each pentest runs through a pipeline of specialized agents:
-
Reconnaissance (Web) or Endpoint Grouping (API)
- Maps your application structure
- Identifies technologies and authentication flows
- Plans subsequent testing phases
-
Security Testing
- Multiple agents test in parallel
- Testing focuses on OWASP Top 10 vulnerabilities
- Findings appear in real-time
-
Processing
- Deduplicating similar findings
- Consolidating vulnerabilities across agents
- Enriching with remediation guidance
-
Complete
- Final vulnerability list with priorities
- Report generation available
Understanding Pentest Results
After your pentest completes:
- Review the summary - See vulnerability counts by severity
- Prioritize findings - Focus on Critical and High severity first
- Read remediation guidance - Each finding includes fix recommendations
- Generate reports - Download for team review or compliance
For detailed guidance, see Understanding Reports.
Scheduled Pentests
Automated pentests run based on your configured frequency (daily, weekly, or monthly). You can view upcoming scans, reschedule them, or run them immediately from the Schedule page.
See Managing Schedules for details on viewing and rescheduling automated pentests.
Next Steps
Last updated: February 1, 2026