Adding Applications
Register your product and configure attack surfaces for security testing
An application represents a single product or service with a unified backend. Register one application per product—not separate entries for your web dashboard and API. For more details, see Core Concepts: Application.
Application Basics
Start by providing basic information about your application:
- Name - A friendly identifier for your product (e.g., "Production App", "Staging Environment")
- Description - Optional context for your team
- Environment - Select the deployment environment:
| Environment | Description | Default Testing |
|---|---|---|
| Production | Live customer-facing systems | Active (safe checks only) |
| Staging | Pre-production testing environment | Aggressive (includes exploitation) |
| Development | Local or dev environments | Aggressive (includes exploitation) |
The environment you select affects the default testing intensity. Production environments use safer testing by default to avoid service disruption.
Select Attack Surfaces
Choose which interfaces of your application to test:
| Surface | When to Enable |
|---|---|
| Web Application | Your product has a user-facing website or web app |
| REST API | Your product exposes REST/GraphQL endpoints |
Most modern SaaS products have both surfaces—a web dashboard and an API that share users, data, and business logic. Enable both for complete coverage.
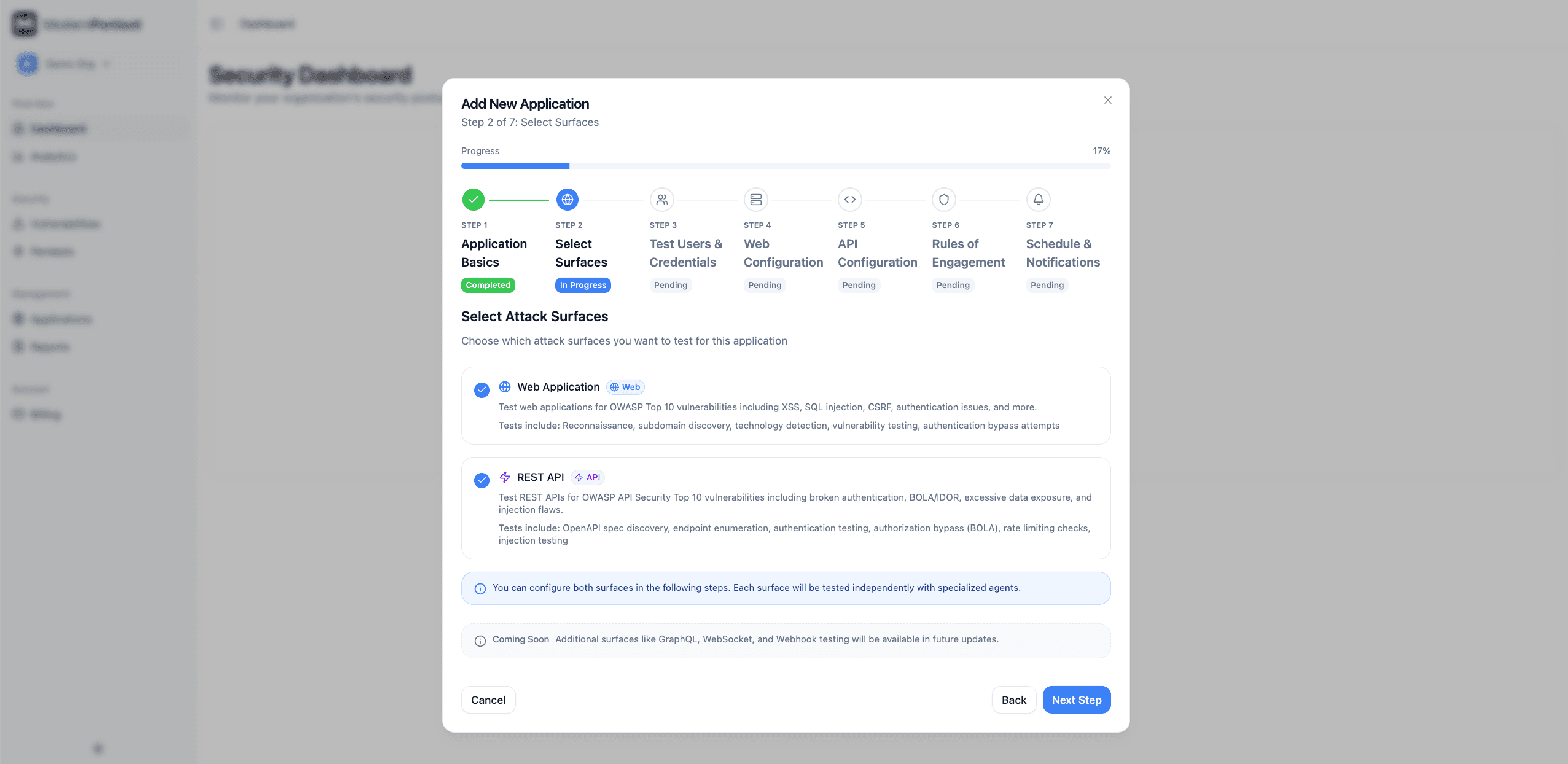
At least one surface must be selected. Your selection determines which configuration steps appear next.
Test Users & Credentials
Test users are defined once and shared across all surfaces. This enables consistent authorization testing across your web app and API.
Authentication Strategy:
| Strategy | Description | Best For |
|---|---|---|
| Public | No authentication required | Public-facing apps without login |
| Pre-configured | Provide existing test accounts | Most applications (default) |
| Open Registration | Agents create accounts automatically | Coming soon |
Adding Test Users:
For pre-configured authentication, add one or more test accounts:
- Email/Username - Login credentials
- Password - Account password
- Role - User role for authorization testing (e.g., "admin", "user", "viewer")
Use dedicated test accounts with realistic permissions. Never use production admin credentials or real user accounts.
Why shared users? The same credentials test both web login and API authentication, enabling cross-surface authorization testing. For example, we can verify that a "user" role can't access admin endpoints on both the web app and API.
Web Surface Configuration
This step appears if you selected Web Application.
Configure how we access your web application:
Application URL
Enter the root URL of your web app (e.g., https://app.yourcompany.com)
Authentication Strategy:
| Strategy | Description |
|---|---|
| Public | No authentication needed for testing |
| Shared Users | Uses credentials from Test Users step (recommended) |
| Custom | Web-specific credentials different from shared users |
For most applications, Shared Users is recommended—it uses the test accounts you configured in the previous step and enables cross-surface testing.
REST API Configuration
This step appears if you selected REST API.
Configure your API for testing:
Base URL
Enter your API's root URL (e.g., https://api.yourcompany.com)
OpenAPI Specification
Providing your OpenAPI spec enables deeper testing. Choose how to provide it:
| Method | Description |
|---|---|
| Auto-discover | We scan 30+ common paths (/openapi.json, /swagger.json, etc.) |
| URL | Direct link to your spec |
| Upload | Upload a JSON or YAML file (max 5MB) |
| Paste | Copy and paste spec content |
Don't have an OpenAPI spec? Select auto-discover—we can still test your API through reconnaissance, but coverage will be more limited.
Authentication Strategy:
| Strategy | Description |
|---|---|
| Public | No authentication needed |
| Shared Users | AI discovers your auth flow using test credentials (recommended) |
| Static | Manual credential configuration |
For Static authentication, choose your auth type:
- API Key - Header name and value
- Bearer Token - JWT or access token
- OAuth 2.0 - Token URL, client ID, secret, and scope
- Basic Auth - Username and password
Rules of Engagement
Configure how aggressively we test your application:
Testing Intensity:
| Level | Description | Recommended For |
|---|---|---|
| Passive | Reconnaissance only, no active testing | Sensitive production systems |
| Active | Safe vulnerability checks | Production environments |
| Aggressive | Includes exploitation attempts | Staging and development |
Testing intensity is auto-set based on your environment selection, but you can override it here.
Test Types:
| Type | Description | Default |
|---|---|---|
| Recon | Asset discovery and mapping | Always enabled |
| Scanning | OWASP Top 10 vulnerability checks | Enabled |
| Exploitation | Attempt to exploit found vulnerabilities | Requires approval |
Excluded Paths
Specify paths to skip during testing (comma-separated):
/logout- Avoid logging out test users/delete-account- Prevent destructive actions/admin/danger-zone- Skip sensitive admin functions
All testing is documented for compliance purposes. See SOC 2 Reports for details.
Schedule & Notifications
Configure when and how often we test:
Scan Frequency:
| Frequency | Availability |
|---|---|
| Manual | On-demand only (Enterprise) |
| Monthly | All plans |
| Weekly | Professional and above |
| Daily | Coming soon |
Preferred Testing Window:
| Window | Hours | Recommended |
|---|---|---|
| Business Hours | 9am - 5pm | For monitored testing |
| Off-Hours | 6pm - 8am | Minimal user impact |
| Anytime | 24/7 | Maximum flexibility |
Off-hours testing is recommended for production environments to minimize impact on users.
Notifications:
- Email - Receive alerts when pentests complete or critical findings are discovered
- Severity Threshold - Choose to be notified for critical/high only or all findings
After adding your application, you can manage its schedule from the Schedule page—view upcoming pentests, reschedule them, or run immediately.
Automatic Platform Detection
You don't need to configure platform-specific settings. Our AI agents automatically detect and test:
| Platform | What We Detect | What We Test |
|---|---|---|
| Supabase | URL patterns, SDK usage | RLS policies, storage buckets, edge functions |
| Firebase | Config objects, SDK imports | Firestore rules, RTDB permissions, storage rules |
| Vercel/Next.js | Headers, deployment patterns | NEXT_PUBLIC_ exposure, API routes, middleware |
| Convex | Client configuration | Database access, function permissions |
Platform detection happens during each pentest. If you add Supabase to your project later, we'll automatically detect and test it—no configuration changes needed.
Learn more in Platform Agents.
Next Steps
Last updated: February 1, 2026